Now that we’re almost through the first month of 2022, it’s a good opportunity for us to take a look back at 2021 and the accomplishments of the Zero Day Initiative throughout the year. The past year was certainly a year full of its challenges, but we also celebrated some unique achievements in our busiest year ever. In addition to publishing the highest number of advisories in the history of the program, we hit our first million-dollar Pwn2Own in April. And as if that weren’t enough, we did it again in the fall as Pwn2Own Austin also exceeded the $1,000,000 threshold.
To say these were superlative events is an understatement. In the spring edition, we saw multiple Exchange exploits demonstrated, including ProxyShell. We saw 0-click remote code execution demonstrated on Zoom messenger and a 1-click code execution on Microsoft Teams. That’s on top of the Chrome, Edge, and Safari web browsers all getting compromised, too. The fall event had its own highlights, with the Samsung Galaxy, multiple routers, NAS devices, and printers being exploited. Watching a printer rock out some AC/DC after an exploit was just a bonus.
Of course, that should not detract from the great submissions we received throughout the year. We’ve already listed our Top 5 bugs from 2021, but that barely scratches the surface of the tremendous research disclosed to ZDI this past year. And while we are always impressed with the quality of research submitted to the program, ZDI’s own researchers stepped up this year and account for 31% of all published advisories. Still, we’re super thankful for our global community of independent researchers, and we congratulate the 25 researchers to achieve reward levels in 2021. We had six people reach Platinum status, two reach Gold, 4 Silver, and 13 Bronze. The work and submissions from our community of independent researchers are key to our success, and we thank all of them for their continued trust in our program.
Our program also wouldn’t work without vendors generating and releasing fixes for the vulnerabilities we report to them. The ZDI would not be able to sustain this level of advisories – and thus, better protections for Trend Micro customers – without the contributions of researchers and vendors, and we thank them for all they do.
Let’s take a look at some of the more interesting stats from 2021.
By the Numbers
In 2021, the ZDI has published 1,604 advisories – the most ever in the history of the program. This is the second year in a row where eclipsed our previous all-time total. While it’s unlikely we’ll keep up a record-breaking pace for the third year in a row, it does speak to the overall health of the program. Here’s how that number of advisories stacks up year-over-year.
Figure 1 - Published Advisories Year-Over-Year
Coordinated disclosure of vulnerabilities continues to be a successful venture. While 2020 saw our largest percentage of 0-day disclosures, the number declined in 2021 to be in line with our “average” number of disclosures from previous years. The 137 0-day disclosures this past year represents 8.5% of our total disclosures – down from 18.6% the year before. This is a positive trend, and we hope it continues moving forward.
Figure 2 - 0-day Disclosures Since 2005
Here’s a breakdown of advisories by vendor. The top vendors here should not be surprising, although it is interesting to see Siemens in the top 5. We purchase quite a few ICS-related bugs throughout the year, and our Pwn2Own Miami competition focuses solely on ICS and SCADA-related bugs. In all, we disclosed 586 ICS-related bugs in 2021 – roughly 36.5% of the total number of advisories published by ZDI. As far as enterprise software goes, it’s no surprise at all to see Microsoft on top of the list again this year. In fact, 19.6% of all bugs addressed by Microsoft in 2021 came through the ZDI program, and we remain a significant source of bugs reported to Adobe, Apple, and others.
Figure 3 - Advisories per vendor for 2021
We’re always looking to acquire impactful bugs and, looking at the CVSS scores for the advisories we published in 2021, we did just that. A total of 74% of these vulnerabilities were rated Critical or High severity.
Figure 4 - CVSS 3.0 Scores for Published Advisories in 2021
Here’s how that compares year-over-year going back to 2015:
Figure 5 - CVSS Scores from 2015 through 2021
As you can see, after 2018 we made a conscious effort to ensure we were acquiring vulnerabilities that have the greatest impact on our customers. We’ll continue to do that in the coming year as well. We continually work with Trend Micro customers to determine which products they have deployed in their enterprise. That helps us shape our purchasing and research directions.
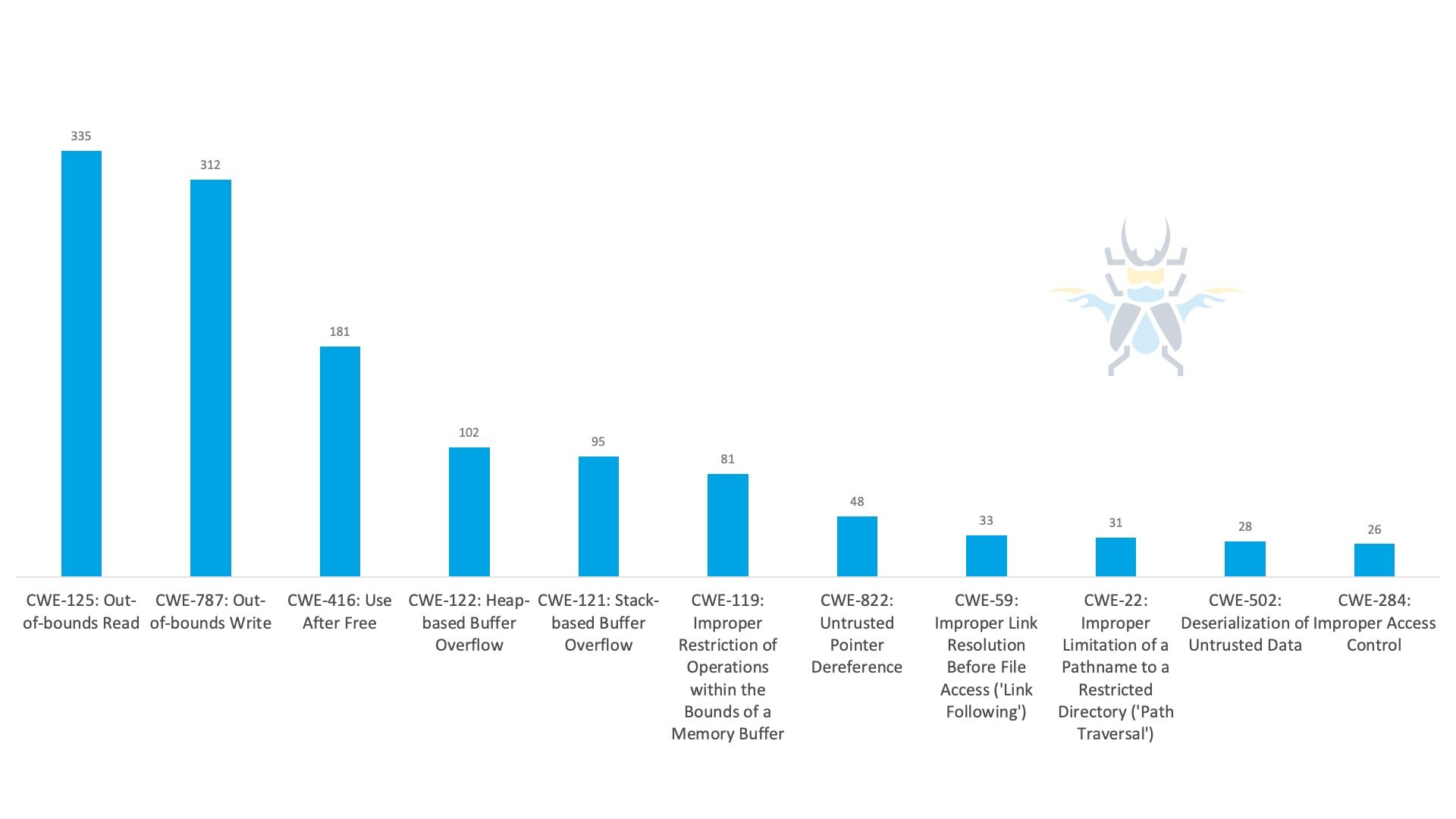
When it comes to the types of bugs we’re buying, here’s a look at the top 10 Common Weakness Enumerations (CWEs) from 2021:
Figure 6 - Top 10 CWEs from 2021 Published Advisories
It’s no surprise to see two CWEs related to out-of-bounds accesses at the top of the list, nor is it surprising to see this followed by use-after-free (UAF) bugs and heap-based buffer overflow issues. In fact, the top seven CWEs are all related to memory corruption somehow. A total of 72% of the advisories we published in 2021 were related to memory corruption bugs. Clearly, we as an industry still have work to do in this area.
Looking Ahead
Moving into the new year, we anticipate staying just as busy. We currently have more than 600 bugs reported to vendors awaiting disclosure. We have Pwn2Own Miami and Pwn2Own Vancouver just on the horizon – and both will (fingers crossed) have participation on location. This year will be the 15th anniversary of Pwn2Own in Vancouver, and we’re planning some very special treats as a way to celebrate. Don’t worry if you can’t come to the contest themselves, as we’ll be streaming the events on YouTube and Twitch as they occur. If you ever wanted to attend Pwn2Own but couldn’t, you have a chance to watch them online.
In the coming year, we’re also looking to expand our program by acquiring bugs with an even bigger impact on our customers and the global community. Expect to see us purchasing more bugs in cloud-native applications, the Linux operating system, and anything else that poses a significant threat to our customer’s networks and resources. We look forward to refining our outreach and acquisition efforts by further aligning with the risks our customers are facing to ensure the bugs we squash have the biggest impact on our customers and the broader ecosystem.
In other words, 2022 is shaping up to be another exciting year with impactful research, great contests, and real information you can use. We hope you come along for the ride. Until then, be well, stay tuned to this blog, subscribe to our YouTube channel, and follow us on Twitter for the latest updates from the ZDI.