Welcome to the first ever Pwn2Own Automotive: live from Tokyo January 24-26, 2024! We’ll be updating this blog in real time as results become available. We have a full schedule of attempts today, so stay tuned! All times are Japan Standard Time (GMT +9:00).
SUCCESS - Sina Kheirkhah was able to execute his attack against the ChargePoint Home Flex for $60,000 and 6 Master of Pwn Points.
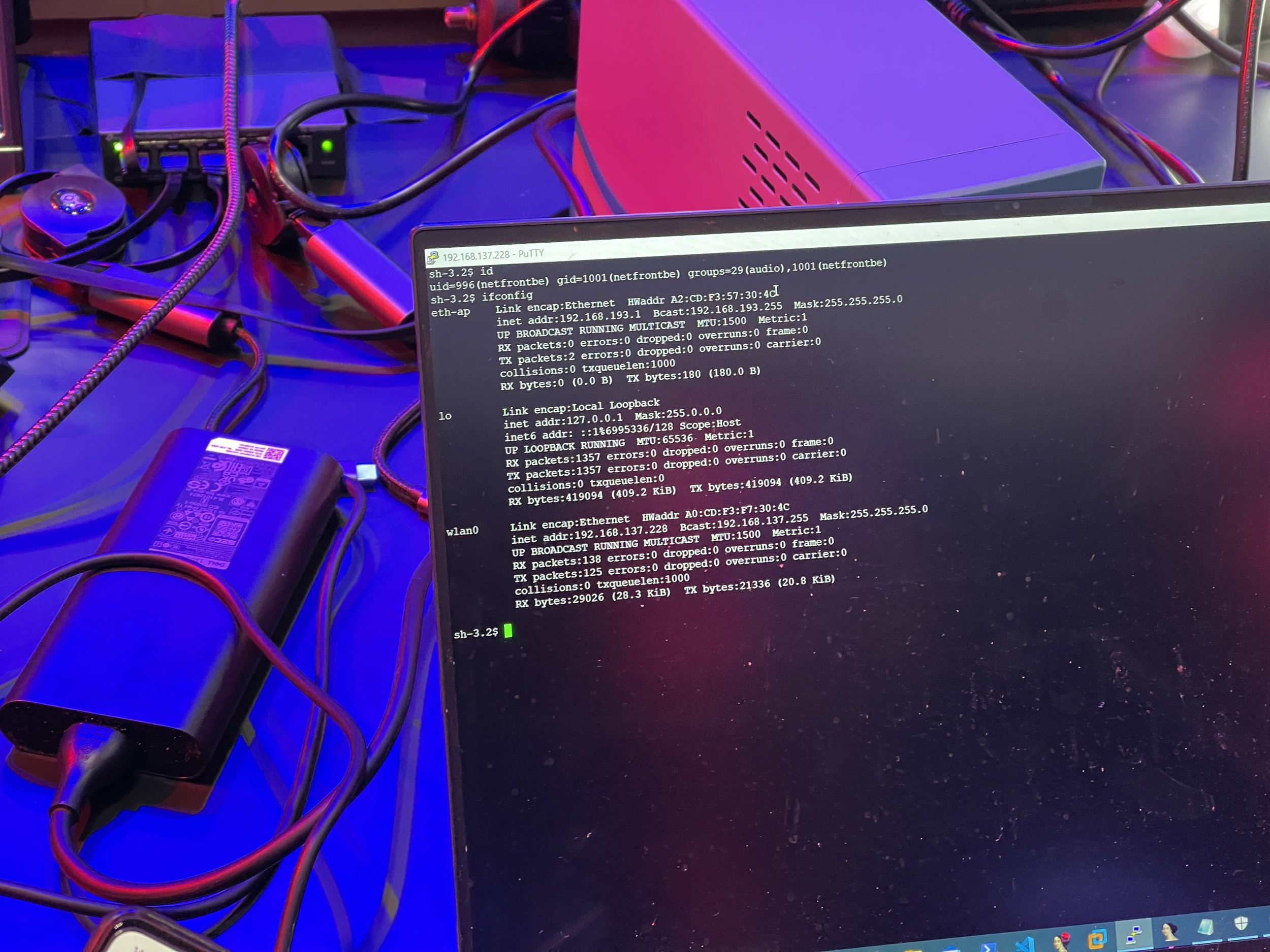
COLLISION - Rob Blakely from Cromulence successfully executed his attack on Automotive Grade Linux. However, an n-day exploit was used in the attack. He still earns $47,500 and 3.75 Master of Pwn Points.
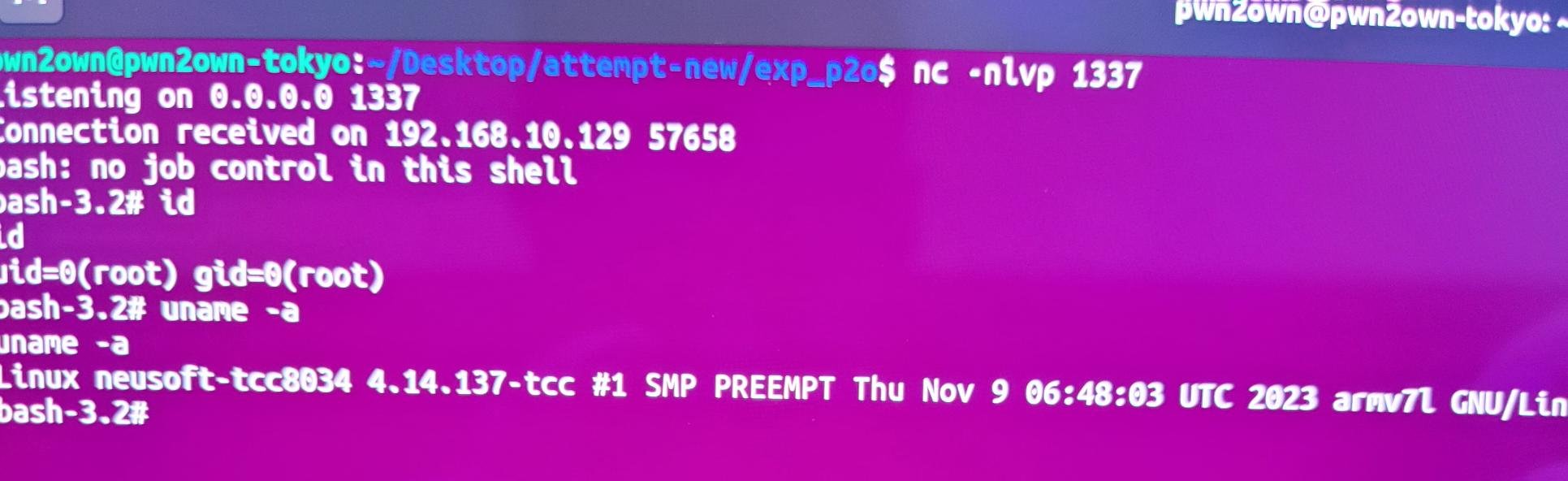
SUCCESS - The PCAutomotive Team successfully targeted the Alpine Halo9 iLX-F509 with a UAF exploit for $40,000 and 4 Master of Pwn Points.
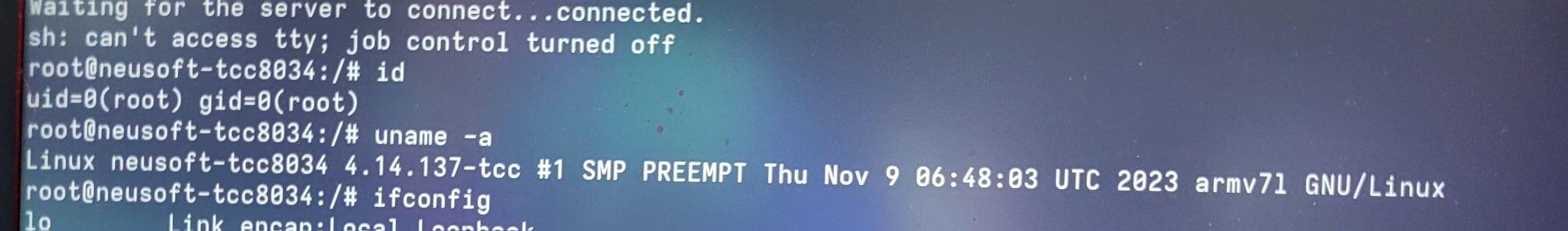
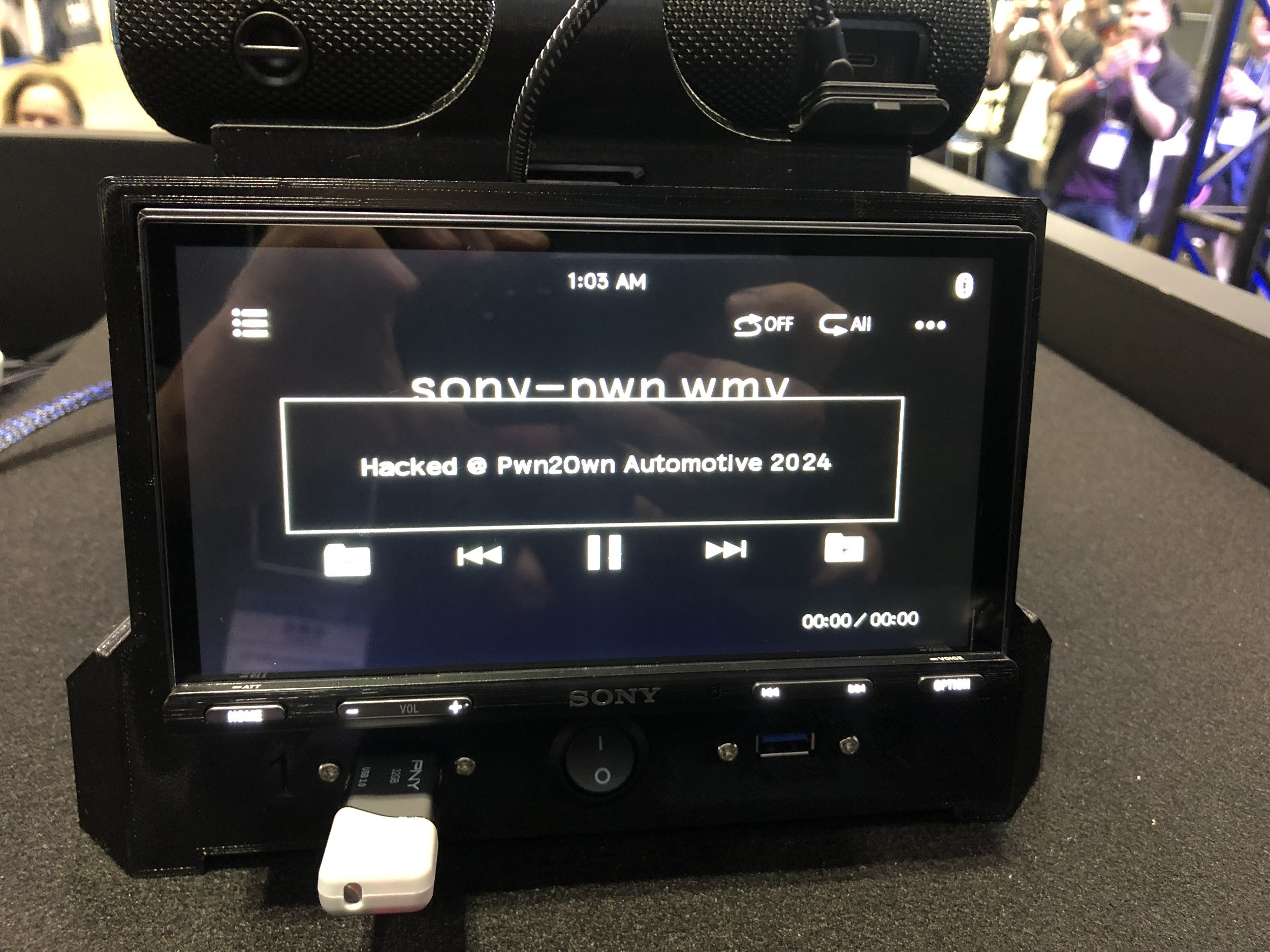
SUCCESS - Tobias Scharnowski and Felix Buchmann of fuzzware.io executed their attack against the Sony XAV-AX5500 for $40,000 and 4 Master of Pwn Points.
SUCCESS - The Synacktiv Team successfully executed their 3-bug chain against the Tesla Modem. They win $100,000 and 10 Master of Pwn Points.
SUCCESS - Katsuhiko Sato executed his command injection attack against the Alpine Halo9 iLX-F509. As this was a second round win, he wins $20,000 and 4 Master of Pwn Points.
FAILURE - Sina Kheirkhah was not able to get his exploit of the Sony XAV-AX5500 working in the time allotted.
SUCCESS - NCC Group EDG executed a 3-bug chain against the Pioneer DMH-WT7600NEX. They earn $40,000 and 4 Master of Pwn Points.
SUCCESS - The Synacktiv Team used a 2-bug chain against the Ubiquiti Connect EV Station. They earn $60,000 and 6 Master of Pwn Points.
SUCCESS - RET2 Systems executed a 2-bug chain against the Phoenix Contact CHARX SEC-3100. They earn $60,000 and 6 Master of Pwn Points.
SUCCESS - The Midnight Blue / PHP Hooligans team executed a stack-based buffer overflow against the Sony XAV-AX5500. They win $20,000 and 4 Master of Pwn Points.
SUCCESS - Vudq16 and Q5CA from u0K++ successfully executed a stack-based buffer overflow against the Alpine Halo9 iLX-F509. They earn $20,000 and 4 Master of Pwn Points.
BUG COLLISION - The Synacktiv Team used a two-bug chain against the ChargePoint Home Flex. However, the exploit they used was previously known. They still earn $16,000 and 3 Master of Pwn Points.
FAILURE - Sina Kheirkhah was not able to get his exploit of the Phoenix Contact CHARX SEC-3100 working in the time allotted.
SUCCESS - Gary Li Wang used a stack-based buffer overflow against the Sony XAV-AX5500. He wins $20,000 and 4 Master of Pwn Points.
SUCCESS - Synacktiv executed a 2-bug chain against the JuiceBox 40 Smart EV Charging Station. They earn $60,000 and 6 Master of Pwn Points.
BUG COLLISION - Connor Ford of Nettitude executed his attack against the ChargePoint Home Flex. However, his 2-bug chain was previously known. He still earns $16,000 and 3 Master of Pwn Points.
BUG COLLISION - Chris Anastasio and Fabius Watson of Team Cluck successfully attacked the ChargePoint Home Flex. However, the bug they used was previously known. They still earn $16,000 and 3 Master of Pwn Points.
SUCCESS - NCC Group EDG used an improper input validation against the Phoenix Contact CHARX SEC-3100. They earn $30,000 and 6 Master of Pwn Points.
SUCCESS - The Synacktiv team used a 2-bug chain to successfully exploit the Autel MaxiCharger AC Wallbox Commercial. In doing so, they earn $60,000 and 6 Master of Pwn points.
FAILURE - Sina Kheirkhah was not able to get his exploit of the JuiceBox 40 Smart EV Charging Station working in the time allotted.
FAILURE - Unfortunately, Sina Kheirkhah was not able to get his exploit of the Pioneer DMH-WT7600NEX working in the time allotted.
That concludes Day 1 of Pwn2Own Automotive 2024. Check back here and across social media tomorrow for our second day of attempts!