Day One has come to a close and we haven’t had a single failure! We awarded $522,500 for 34 unique bugs on the first day of the contest. Here’s how the Master of Pwn leader board currently sits:
Of course, there’s plenty of time left with some big exploits still to come. Stay tuned for the results from Day Two and Three!
SUCCESS - Team Neodyme used a stack based buffer overflow to exploit the HP DeskJet 2855e. They earn $20,000 and 2 Master of Pwn points.
SUCCESS - Nguyen Hoang Thach (@hi_im_d4rkn3ss), Tan Ze Jian, Lin Ze Wei, Cherie-Anne Lee, Gerrard Tai of STARLabs (@starlabs_sg) used a heap based buffer overflow to exploit the @CanonUSA imageCLASS MF654Cdw. They earn themselves $20,000 and 2 Master of Pwn points.
SUCCESS - @Tek_7987 & @_Anyfun (@Synacktiv) used a stack overflow to achieve rootlevel code execution on the Synology BeeStation Plus. They earn $40,000 and 4 Master of Pwn points in the process.
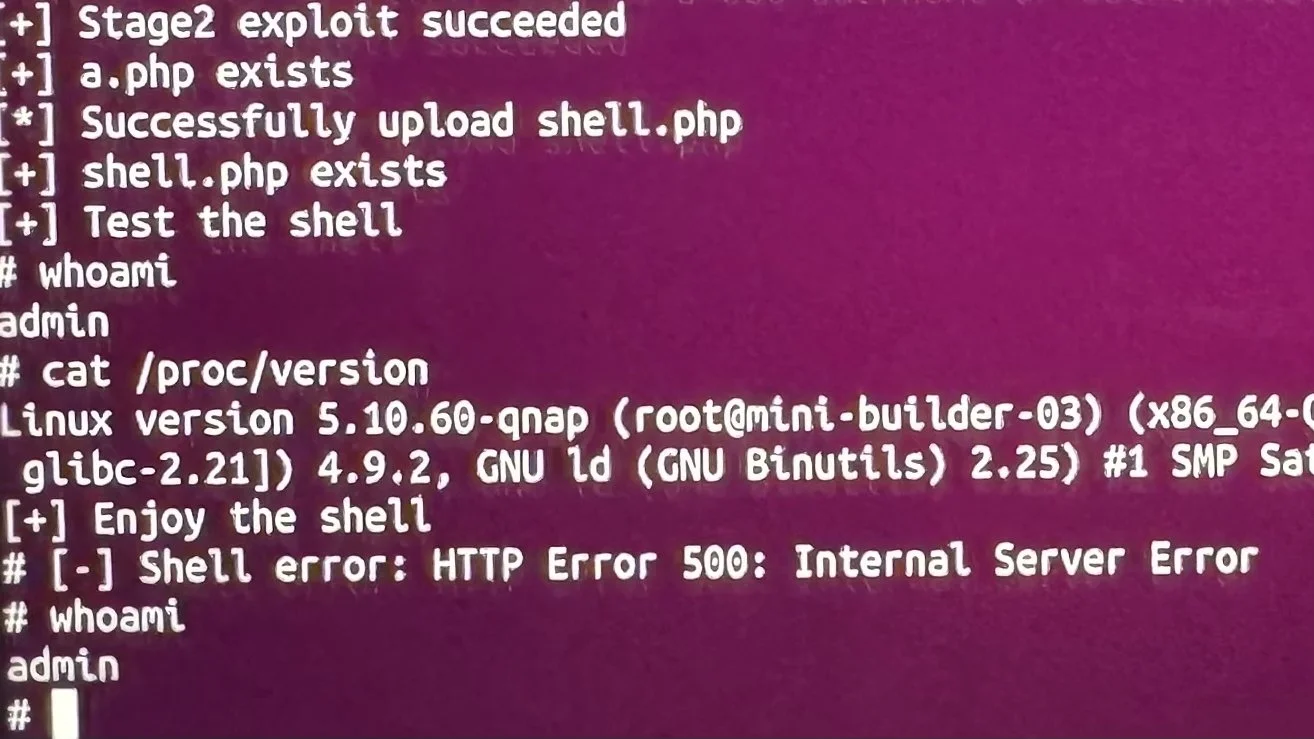
SUCCESS - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS used a magnificent eight different bugs - including multiple injections - to complete their SOHO Smashup of the QNAP Qhora-322 + QNAP TS-453E. They earn $100,000 and 10 Master of Pwn points.
WITHDRAW - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS was withdrawn their attempt of the Philips Hue Bridge.
SUCCESS - SHIMIZU Yutaro (@shift_crops) of GMO Cybersecurity by Ierae, Inc. used a stack based buffer overflow to exploit the Canon imageCLASS MF654Cdw. Their second round win earns them $10,000 and 2 Master of Pwn points.
SUCCESS - Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) used a pair of bugs to gain code execution on the Synology DiskStation DS925+. He earns himself $40,000 and 4 Master of Pwn points
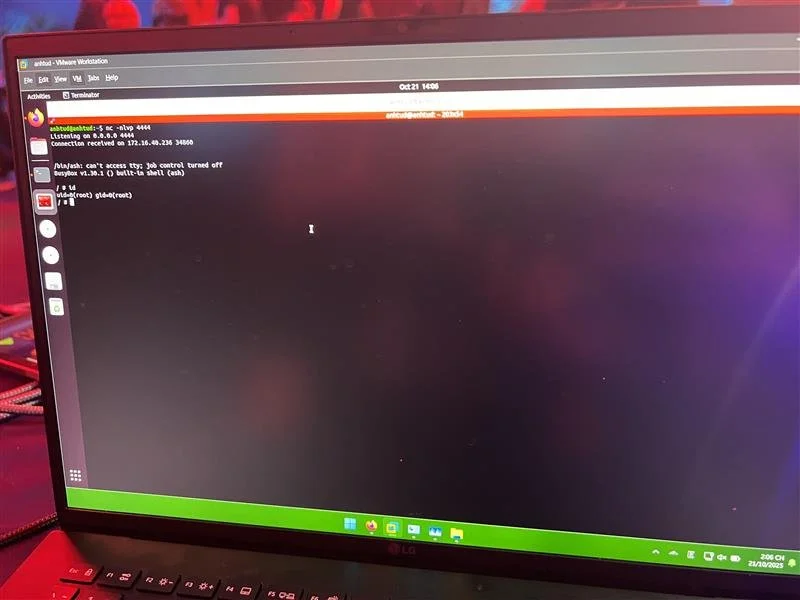
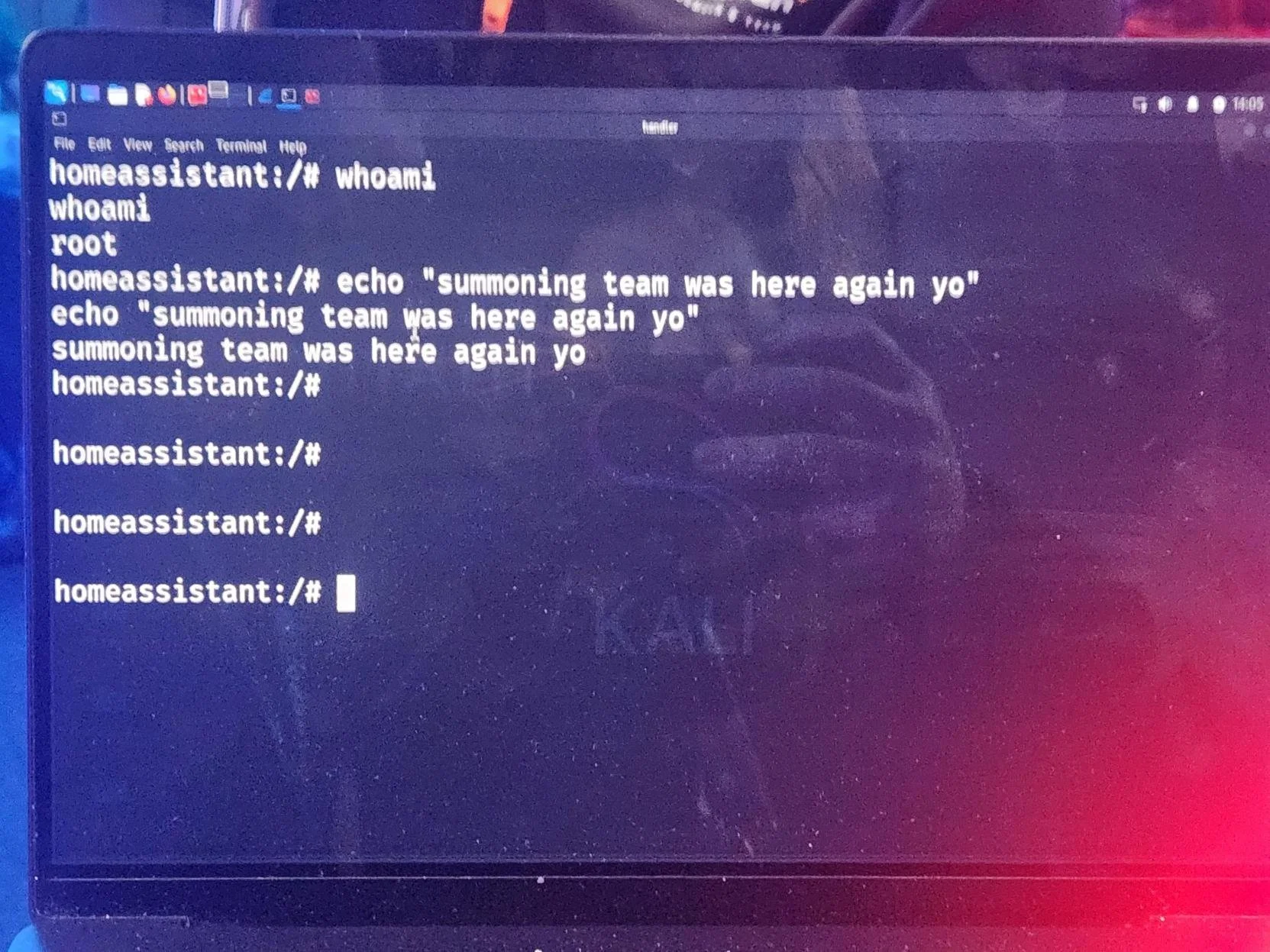
SUCCESS - Stephen Fewer (@stephenfewer) of Rapid7 (@rapid7) used three bugs, including an SSRF and a command injection, to exploit the Home Assistant Green (which isn't actually green). He earns himself $40,000 and 4 Master of Pwn points.
SUCCESS - Sang Nguyen Thien (@gnas0x0018) and mistsu of Team ANHTUD used four bugs - including multiple types overflows and an OOB Read - to exploit the Phillips Hue Bridge. Their outstanding work earns them $40,000 and 4 Master of Pwn points.
SUCCESS/COLLISON - McCaulay Hudson (@_mccaulay) of Summoning Team (@SummoningTeam) successfully exploited the Home Assistant Green with four bugs - one unique SSRF and three bug collisions. They still earn $12,500 and 2.5 Master of Pwn points.
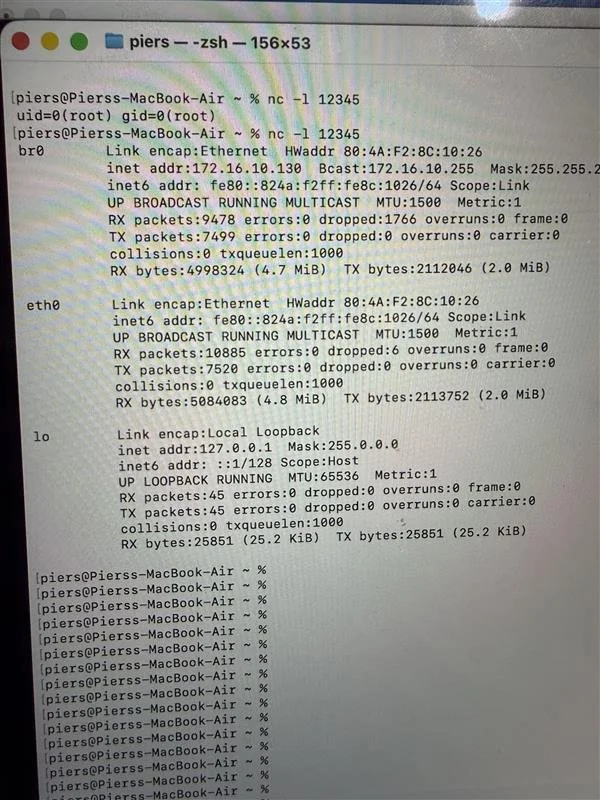
SUCCESS - dmdung (@_piers2) of STAR Labs SG Pte. Ltd used a single OOB access bug to exploit the Sonos Era 300 smart speaker. In doing so, he earns $50,000 and 5 Master of Pwn points.
SUCCESS - Team PetoWorks [SungJun Park (@howrealsung), Wonbeen Im (@D0b6y), Dohyun Kim (@d0now_kim), and Juyeong Lee (@ju_cheda)] used a Release of Invalid Pointer or Reference bug to exploit the Canon printer at Pwn2Own. They $10,000 and two Master of Pwn points for their third round win.
SUCCESS - YingMuo (@YingMuo), HexRabbit (@h3xr4bb1t), LJP (@ljp_tw) from DEVCORE Research Team and nella17 (@nella17tw) from DEVCORE Intern Program used multiple injections and a format string bug(!) to exploit the QNAP TS-453E. Their unique bugs earn them $40,000 and 4 Master of Pwn points.
SUCCESS - Hank Chen (@hank0438) of InnoEdge Labs used an auth bypass and an OOB write to exploit the Phillips Hue Bridge. His second round win earns $20,000 and 4 Master of Pwn points.
SUCCESS - Sina Kheirkhah (@SinSinology) and McCaulay Hudson (@_mccaulay) of Summoning Team (@SummoningTeam) used a pair of bugs to exploit of the Synology ActiveProtect Appliance DP320. That rounds their day off with another $50,000 and 5 more Master of Pwn points.
SUCCESS - Emanuele Barbeno, Cyrill Bannwart, Yves Bieri, Lukasz D., Urs Mueller of Compass Security (@compasssecurity) combined an arbitrary file write and cleartext transmission of sensitive data to exploit the Home Assistant Green. The unique bugs in their third round win earns them $20,000 and four Master of Pwn points.
SUCCESS - Nguyen Ba Nam Dung and Vu Chi Thanh from Team ANTHUD used a single heap based buffer overflow to exploit the Canon imageCLASS MF654Cdw on their third and final attempt. Their fourth round win earns them $10,000 and 2 Master of Pwn points.