Welcome to Day One of Pwn2Own Automotive 2026! Today, 30 entries took the Pwn2Own stage to target the latest automotive systems, as the world’s top security researchers push technology to its limits. Exploits, surprises, and breakthrough discoveries are unfolding.
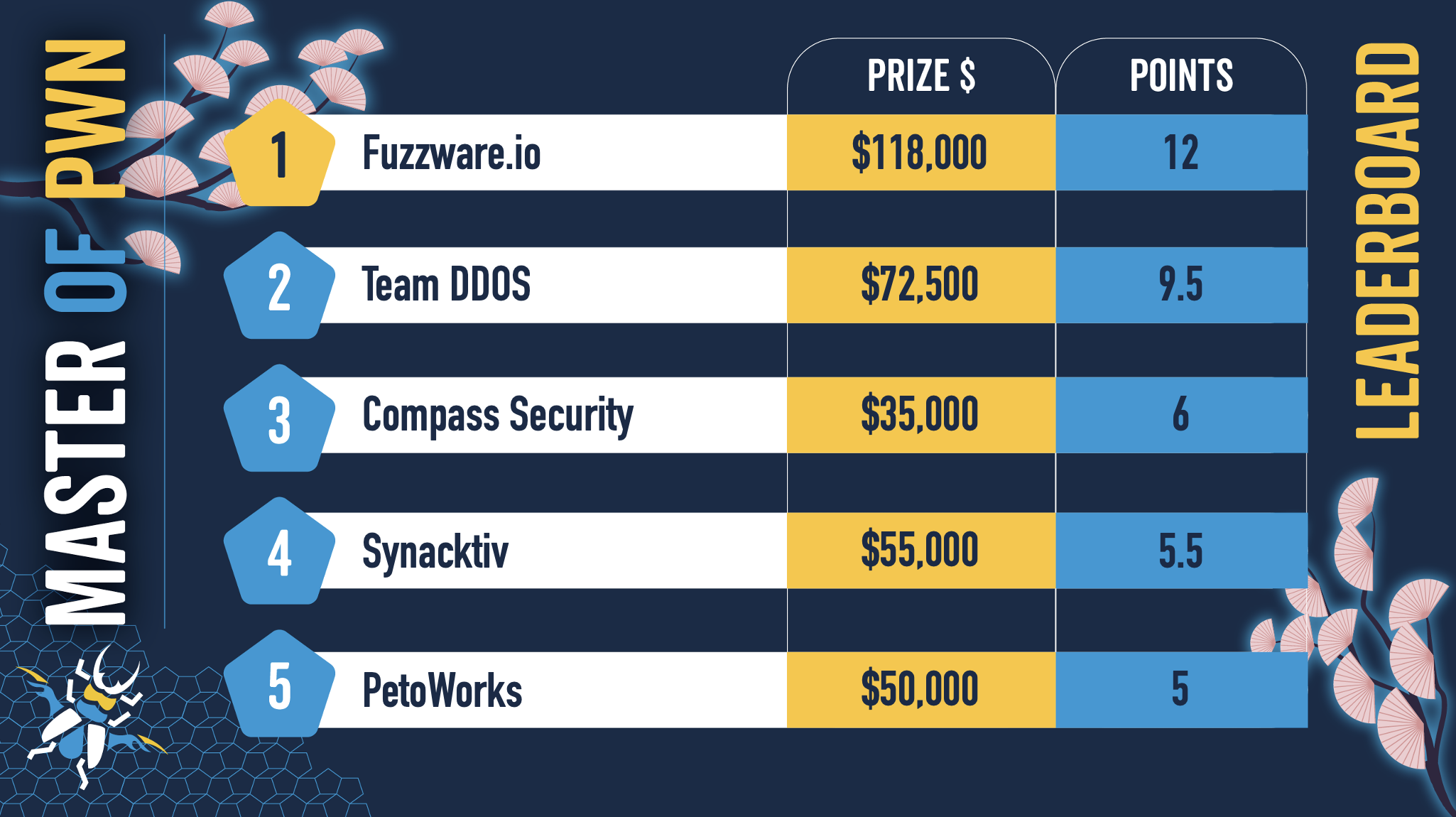
After Day One, we awarded $516,500 for 37 unique 0-days! Fuzzware.io is currently in the lead for Master of Pwn, but Team DDOS is right on their heels. Stay tuned tomorrow for more results and surprises.
Stay up to date by following us on Twitter, Mastodon, LinkedIn, and Bluesky, and join the conversation using #Pwn2Own Automotive and #P2OAuto for continuous coverage.
FAILURE - Unfortunately, Team Hacking Group targeting Kenwood DNR1007XR in the In-Vehicle Infotainment (IVI) category could not get their exploit working within the time allotted.
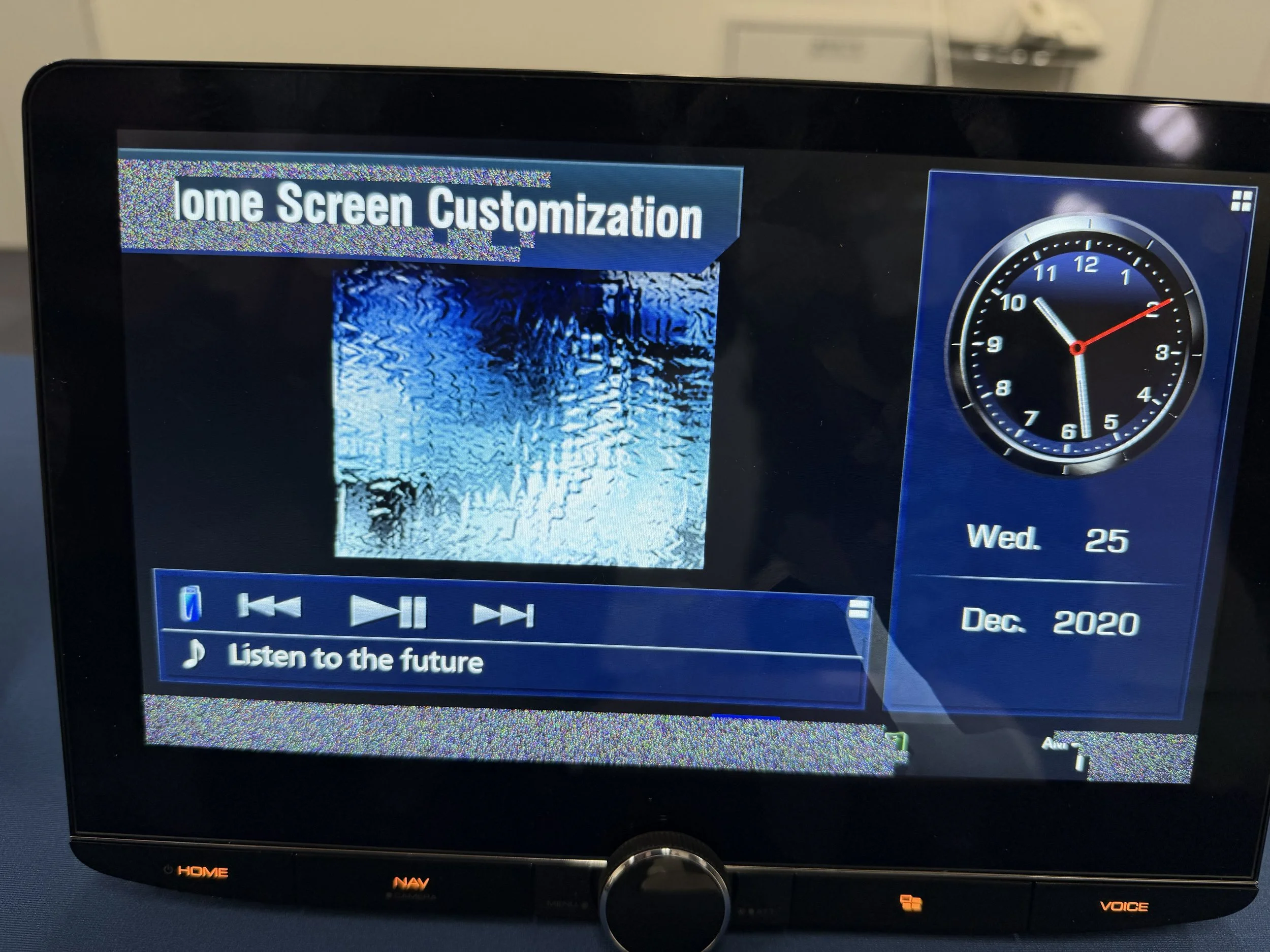
SUCCESS - Neodyme AG (@Neodyme) used a stack based buffer overflow to get a root shell on the Alpine iLX-F511, earning $20,000 USD and 2 Master of Pwn points.
SUCCESS - Fuzzware.io ( @ScepticCtf, @diff_fusion, @SeTcbPrivilege) chained two vulnerabilities (CWE-306, CWE-347) to achieve code execution on the Autel charger and manipulate the charging signal, earning $50,000 USD and 5 Master of Pwn points. Full win with the add-on.
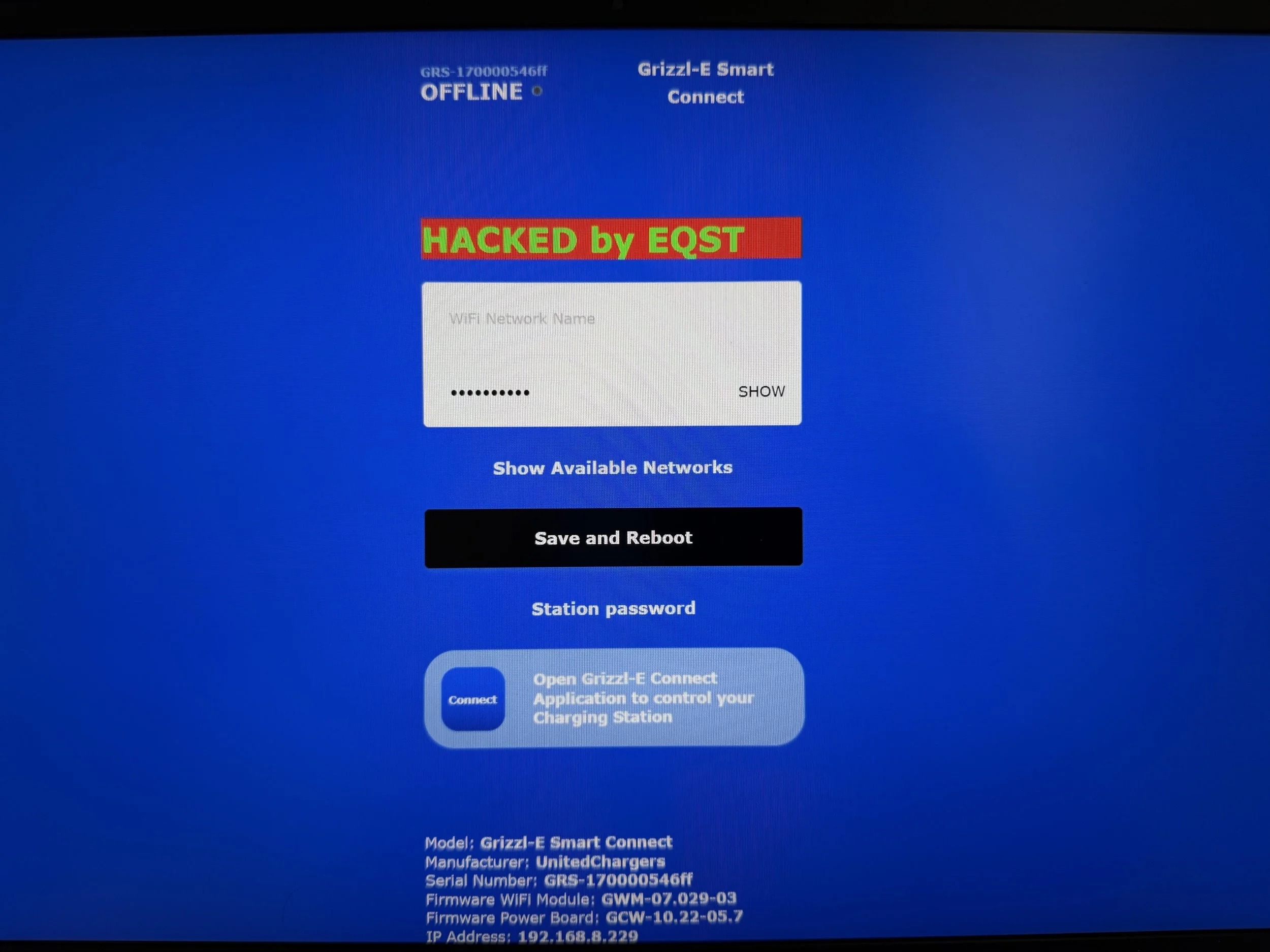
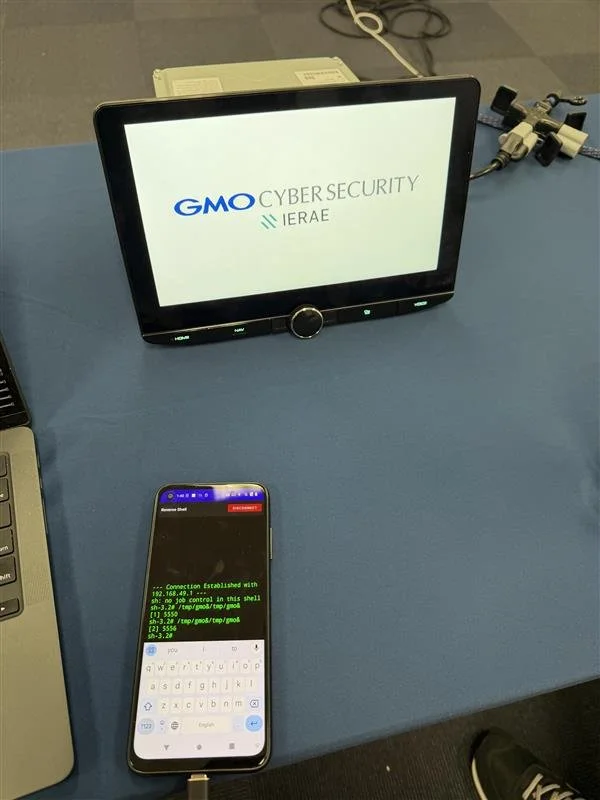
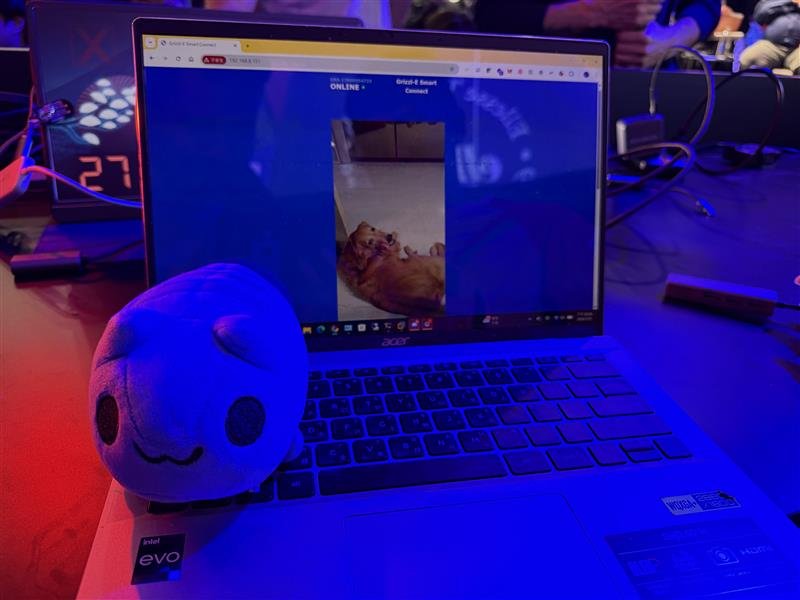
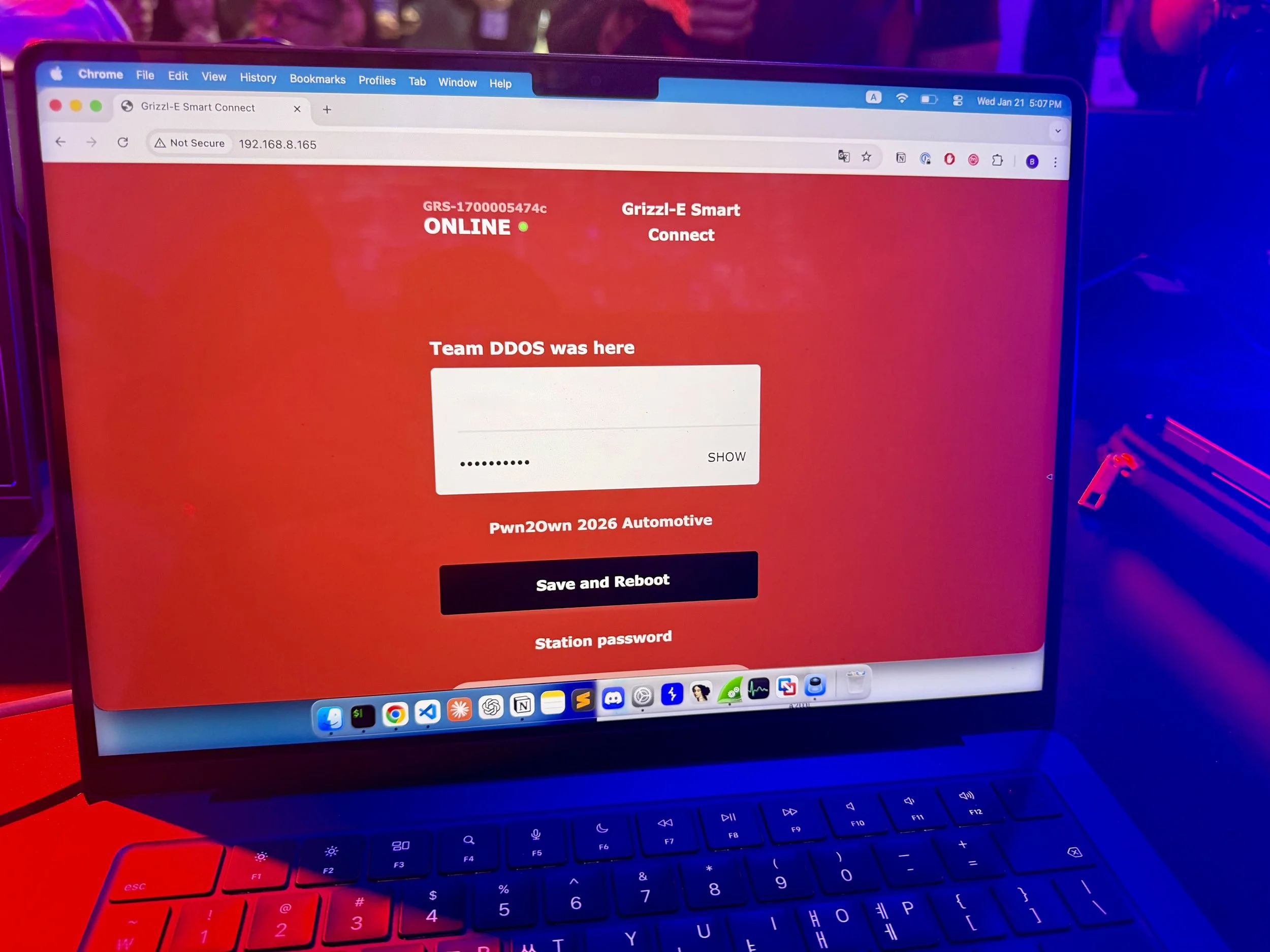
SUCCESS - Taejin Kim (@tae3pwn), Junsu Yeo (@junactually), Sunmin Park (@sunminpark4503), Sungmin Son (@_ssm98), and Hoseok Lee of SKShieldus (@EQSTLab) of 299 exploited a hardcoded credential (CWE-798) to achieve code execution via CWE-494 on the Grizzl-E Smart 40A, earning $40,000 USD and 4 Master of Pwn points.
SUCCESS - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS exploited two bugs, including a command injection, against the ChargePoint Home Flex. Add-on failed, but still earned $40,000 USD and 4 Master of Pwn points.
SUCCESS - Cyrill Bannwart, Emanuele Barbeno, Yves Bieri, Lukasz D., and Urs Mueller of Compass Security (@compasssecurity) exploited one exposed dangerous method/function bug on the Alpine iLX-F511, winning Round 2 for $10,000 USD and 2 Master of Pwn points.
SUCCESS - PetoWorks (@petoworks) chained three bugs - including Denial of Service (DoS), a race condition, and command injection - against the Phoenix Contact CHARX SEC-3150, winning Round 1 for $50,000 USD and 5 Master of Pwn points with the signal manipulation add-on.
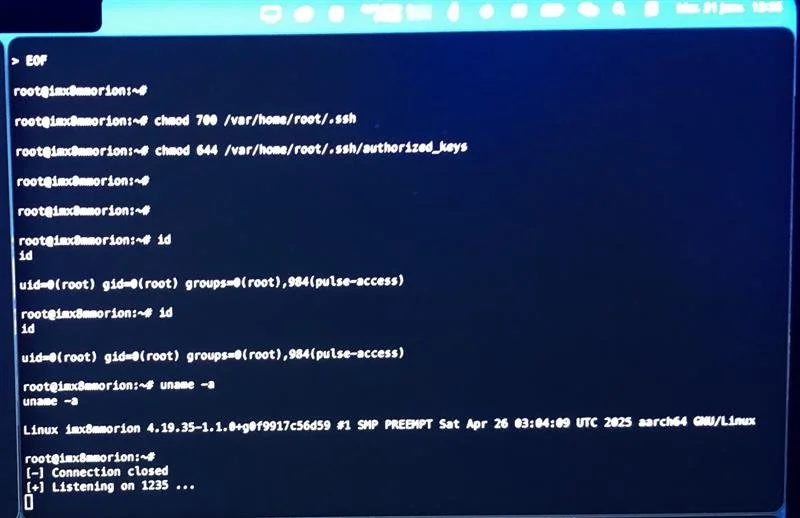
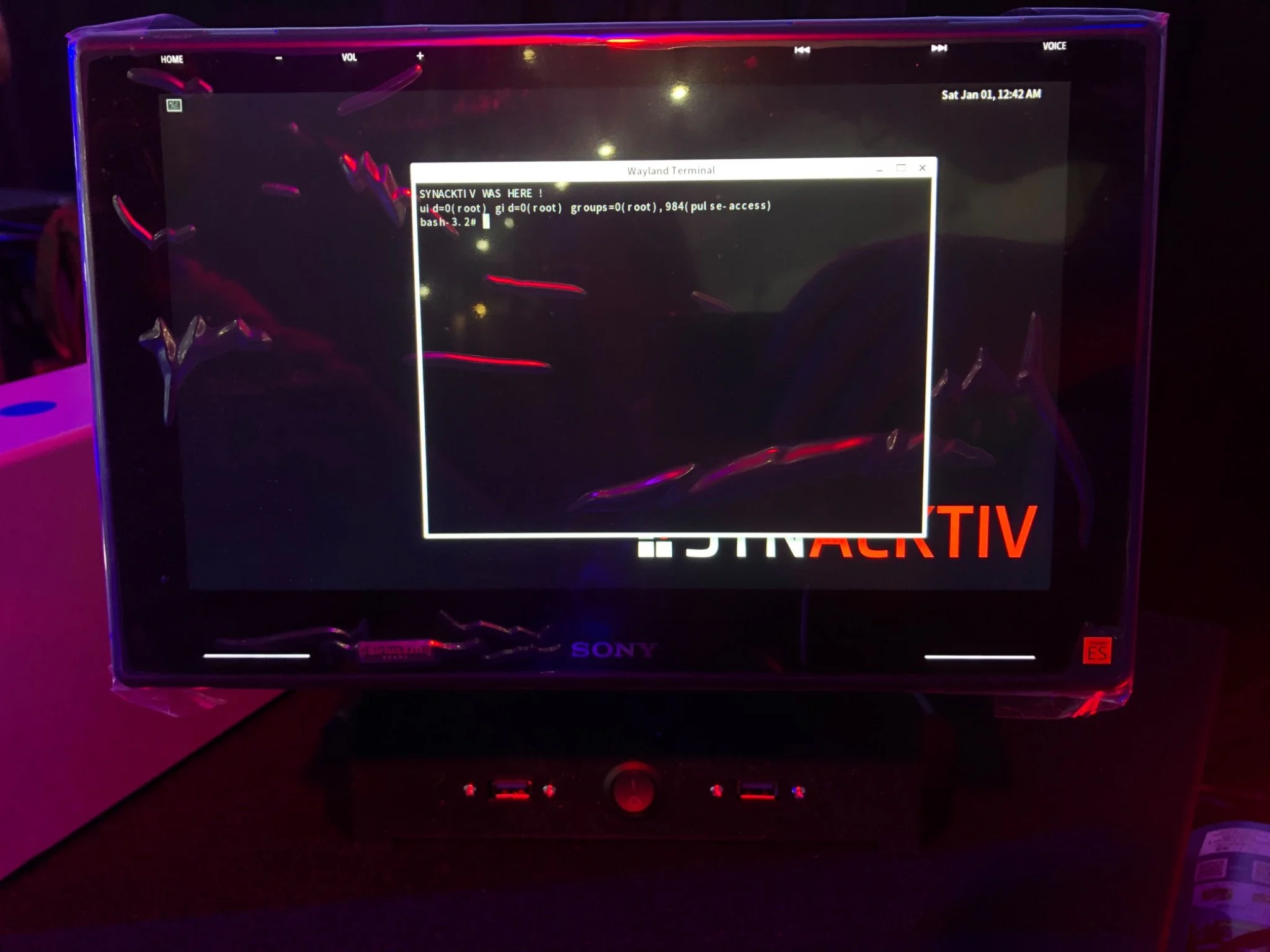
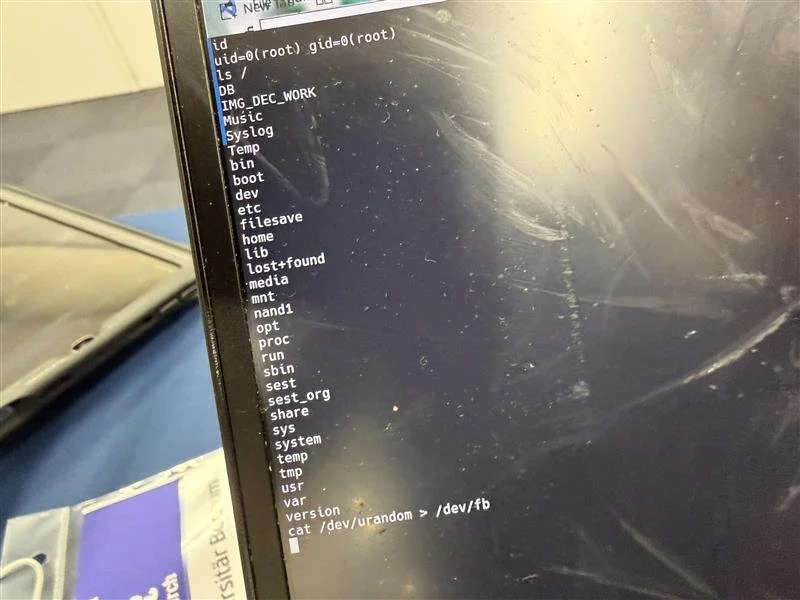
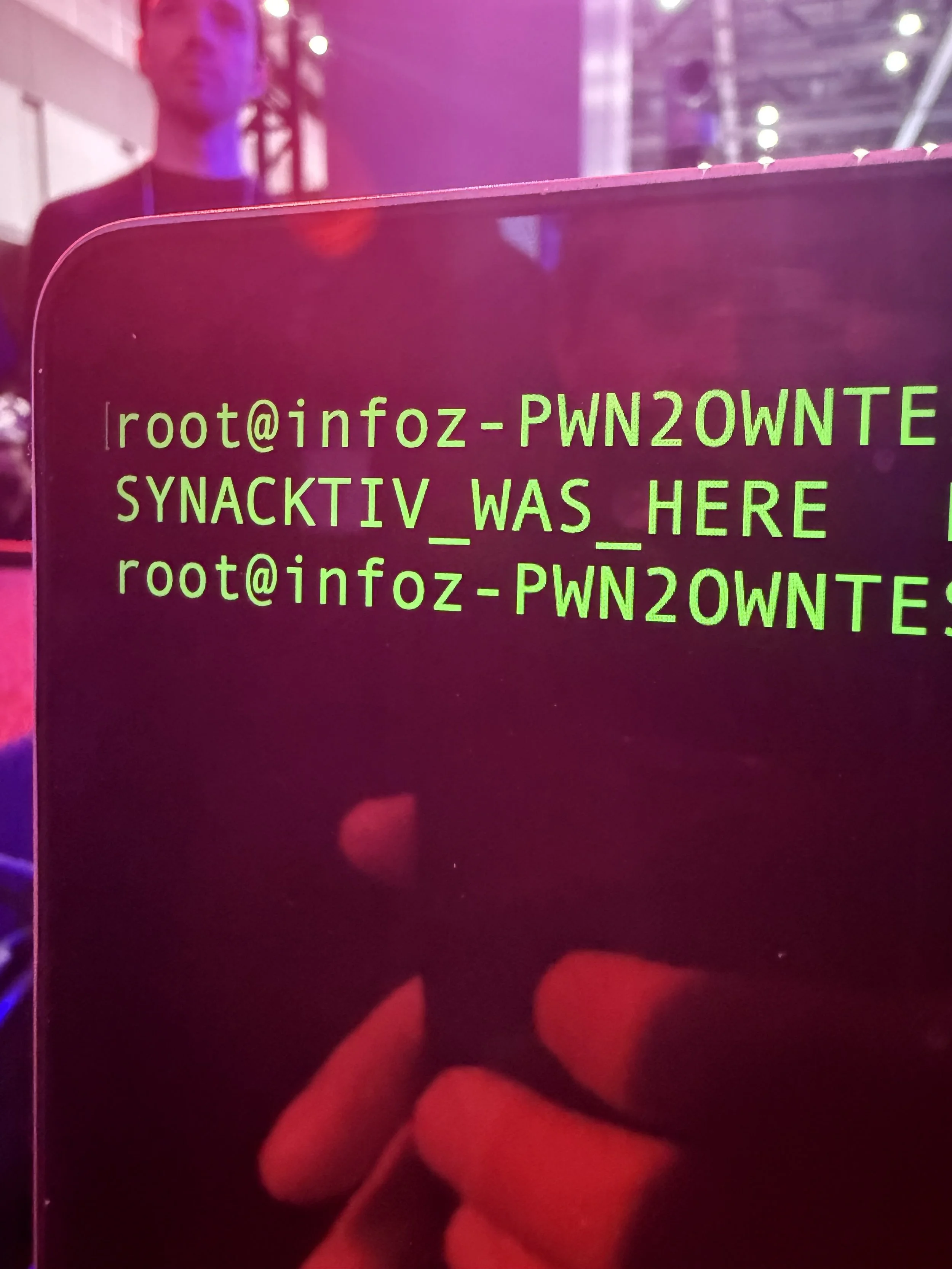
SUCCESS - Synacktiv (@synacktiv) chained three vulnerabilities to gain root-level code execution on the Sony XAV-9500ES, earning a full win of $20,000 USD and 2 Master of Pwn points.
SUCCESS - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io exploited an n-day command injection against Kenwood, earning $8,000 USD and 1 Master of Pwn point.
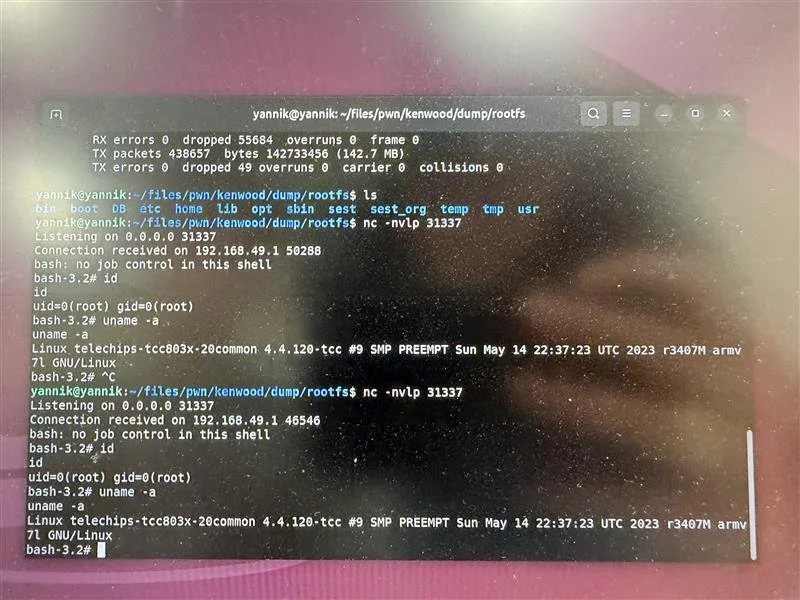
SUCCESS - Yannik Marchand (@kinnay) exploited a single out-of-bounds write to achieve a full win against the Kenwood DNR1007XR, earning $20,000 USD and 2 Master of Pwn points.
FAILURE - Hyunseok Yun, Heaeun Moon, and Eungyo Seo of CIS targeted the Alpine iLX-F511 but were unable to complete their exploit within the allotted time.
SUCCESS / COLLISON - Cyrill Bannwart, Emanuele Barbeno, Yves Bieri, Lukasz D., and Urs Mueller of Compass Security (@compasssecurity) earned $25,000 USD and 4 Master of Pwn points with the Charging Connector Protocol/Signal Manipulation add‑on against the Grizzl‑E Smart 40A, chaining an authentication bypass (CWE‑306) to remote code execution via CWE‑494.
FAILURE - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io targeted the EMPORIA Pro Charger Level 2 with the Charging Connector Protocol/Signal Manipulation add‑on but were unable to complete their exploit within the allotted time.
SUCCESS / COLLISON - Kazuki Furukawa (@N4NU) of GMO Cybersecurity chained three bugs against Kenwood - including an n‑day hard‑coded credential, incorrect permissions on a critical resource, and command injection - to earn $8,000 USD and 1.75 Master of Pwn points.
SUCCESS / COLLISON - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS targeted the Autel MaxiCharger AC Elite Home 40A with the Charging Connector Protocol/Signal Manipulation add-on. Due to a full collision with a previous attempt, they earned $10,000 USD and 2 Master of Pwn points.
SUCCESS / COLLISON - Chumy Tsai (@rm_rf_chumy), Jimmy Liu (@DrmnSamoLiu), and Jim Chen (@asef18766) of Cycraft Technology (@cycraft_corp) targeted the Grizzl-E Smart 40A. Due to a 2-bug collision, they earned $10,000 USD and 2 Master of Pwn points.
SUCCESS - Mia Miku Deutsch (@newbe3e) exploited a stack-based buffer overflow against the Alpine iLX‑F511, earning $10,000 USD and 2 Master of Pwn points.
SUCCESS - Synacktiv (@synacktiv) chained two vulnerabilities - an information leak and an out‑of‑bounds write - to achieve a full win in the Tesla Infotainment USB‑based Attack category, earning $35,000 USD and 3.5 Master of Pwn points.
SUCCESS / COLLISON - Donggeon Kim (@gbdngb12), Hoon Nam (@pwnstar96), Jaeho Jeong (@jeongZero), Sangsoo Jeong (@sangs00Jeong), and Wonyoung Jung (@nonetype_pwn) of 78ResearchLab hit a one‑vulnerability collision against the Alpine iLX‑F511, earning $5,000 USD and 1 Master of Pwn point.
SUCCESS - Giuseppe Calì (_gcali) and 8cf53a459714977f6bb11ee2d90416bf1675fa0e2451d80cf55a06d0b6ac2 of Team Zeroshi exploited five bugs against the Phoenix Contact CHARX SEC-3150, securing a Round 2 win for $20,000 USD and 4 Master of Pwn points.
SUCCESS / COLLISON - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS hit a collision against the Grizzl-E Smart 40A with the Charging Connector Protocol/Signal Manipulation add-on, combining three duplicate bugs and one new bug to earn $22,500 USD and 3.5 Master of Pwn points.
FAILURE - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io targeted Sony XAV-9500ES but were unable to get their exploit working within the allotted time.
FAILURE - Viettel Cyber Security (@vcslab) targeted the ChargePoint Home Flex (CPH50-K) but were unable to get their exploit working within the allotted time.
SUCCESS - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io achieved a full win against the Alpitronic HYC50 - Field Mode, exploiting a single out-of-bounds write to earn $60,000 USD and 6 Master of Pwn points.
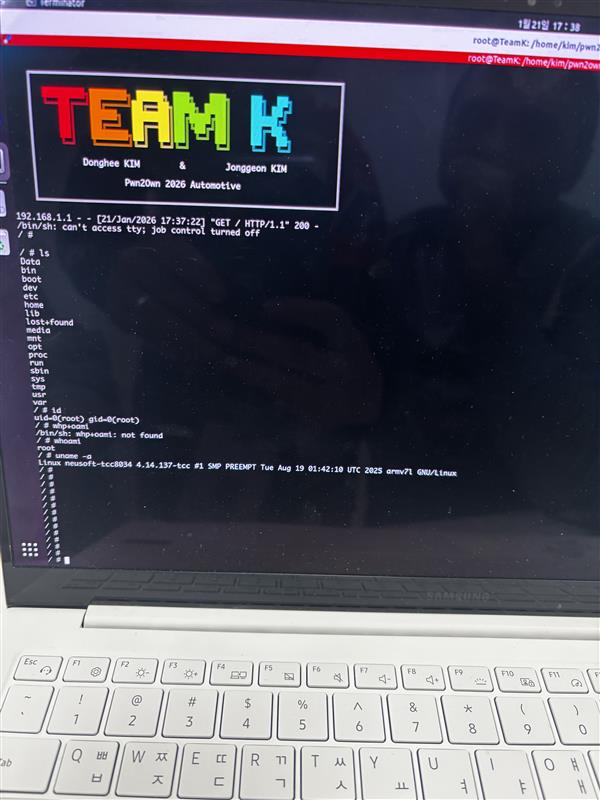
SUCCESS - Dong hee Kim (@heehee_0219_) and Jong geon Kim (@kimjor22) of Team K exploited two vulnerabilities - an out-of-bounds read and a stack-based buffer overflow - against the Alpine iLX-F511, earning $10,000 USD and 2 Master of Pwn points.
SUCCESS - Interrupt Labs (@InterruptLabs) scored a Round 3 win against the Kenwood DNR1007XR, exploiting a unique heap-based buffer overflow to earn $10,000 USD and 2 Master of Pwn points. #Pwn2Own #P2OAuto
FAILURE - Jonathan Conrad (@jwconrad.bsky.social) targeted the Grizzl-E Smart 40A but was unable to reproduce the vulnerability within the allotted time.
SUCCESS / COLLISON - TienPP of FPT NightWolf hit a collision against the Kenwood DNR1007XR, chaining three bugs - including an n‑day hard‑coded credential and two 0‑days (incorrect default permissions and symlink following) - to earn $8,000 USD and 1.75 Master of Pwn points.
SUCCESS - @ExLuck99 and @gr4ss341 of ANHTUD chained two vulnerabilities (CWE‑125 and CWE‑122) to achieve code execution on the Sony XAV‑9500ES, earning $10,000 USD and 2 Master of Pwn points in Round 2.
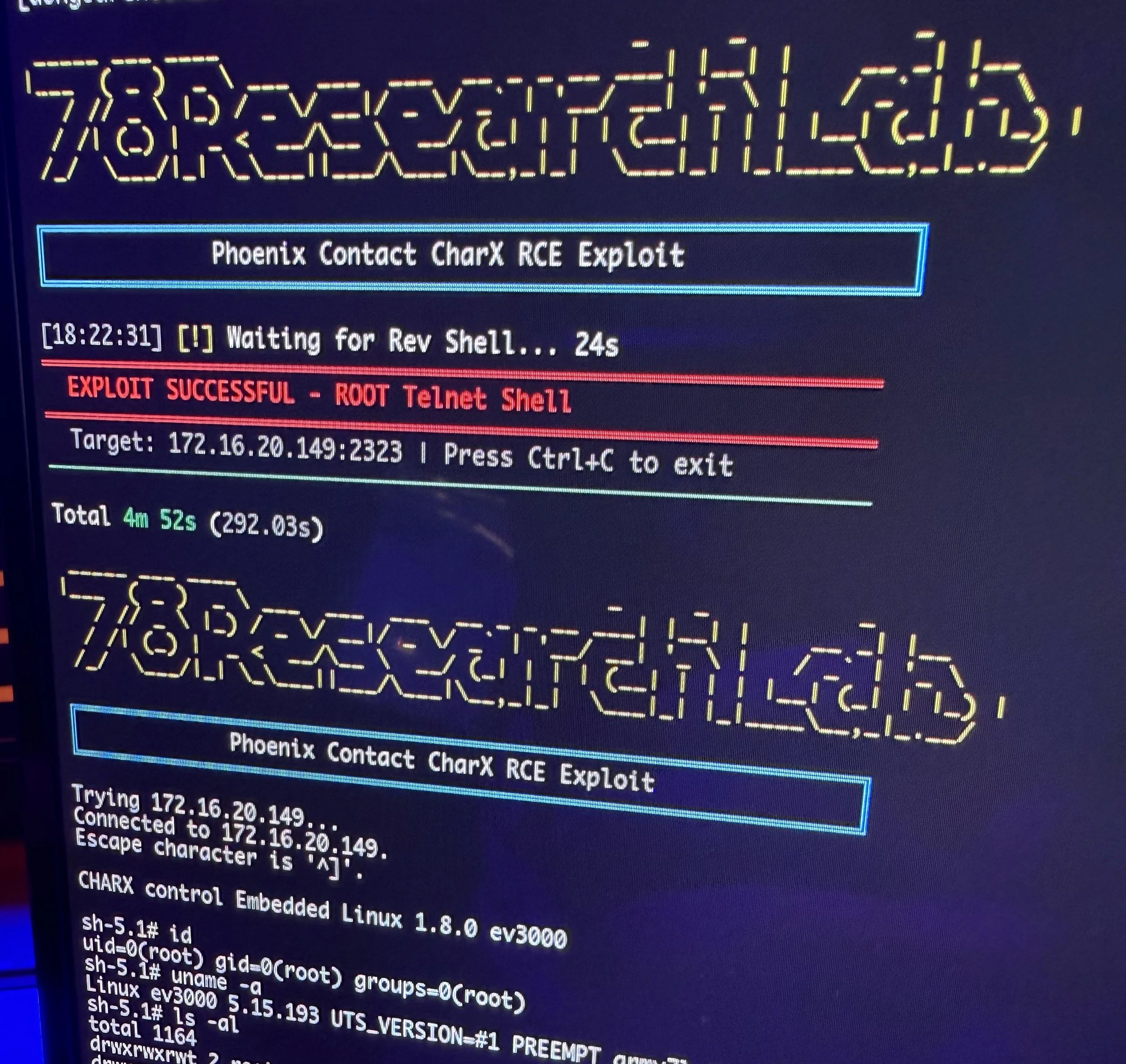
SUCCESS / COLLISON - Donggeon Kim (@gbdngb12), Hoon Nam (@pwnstar96), Jaeho Jeong (@jeongZero), Sangsoo Jeong (@sangs00Jeong), and Wonyoung Jung (@nonetype_pwn) of 78ResearchLab targeted the Phoenix Contact CHARX SEC‑3150, chaining four bugs (two unique and two collisions) to earn $15,000 USD and 3 Master of Pwn points.