The last day of Pwn2Own Automotive 2026 saw the world’s top security researchers take their final shots at the latest automotive systems. Over three days of intense competition, $1,047,000 USD was awarded for 76 unique 0-day vulnerabilities, with bold exploits, clever techniques, and collisions keeping the action thrilling throughout.
By the end, Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io claimed the title of Master of Pwn, earning 28 points and $215,500 USD.
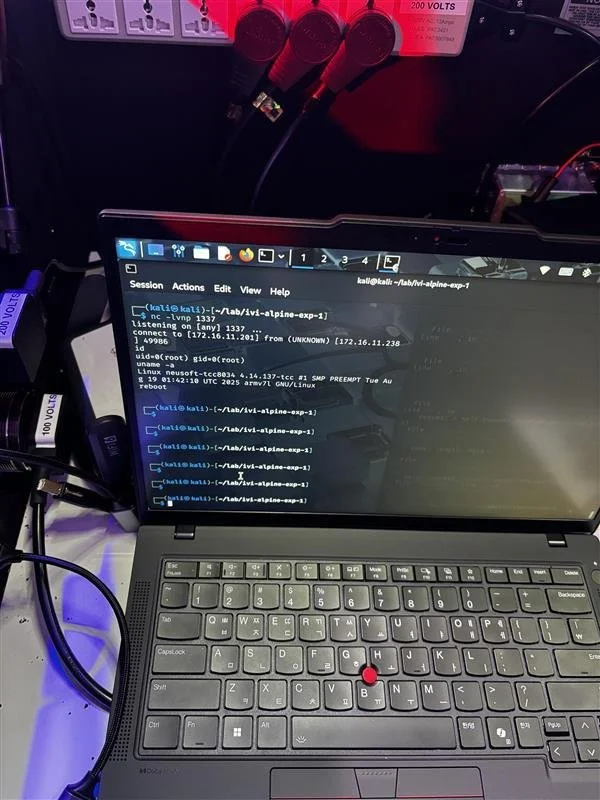
SUCCESS / COLLISON - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io targeted the Alpine iLX-F511, demonstrating one vulnerability previously used by another contestant, earning $2,500 USD and 1 Master of Pwn point. #Pwn2Own #P2OAuto
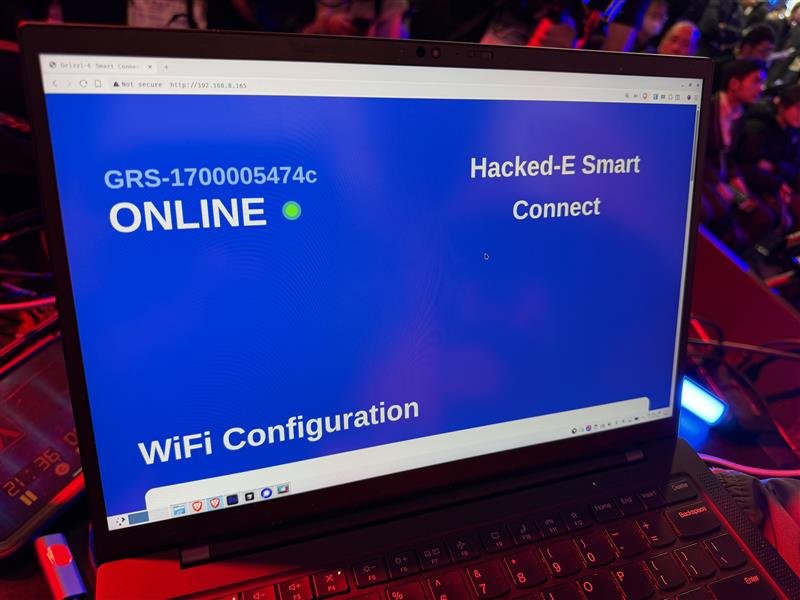
SUCCESS / COLLISON - Slow Horses of Qrious Secure (@qriousec) targeted the Grizzl-E Smart 40A but encountered two bug collisions, still earning $5,000 USD and 2 Master of Pwn points.
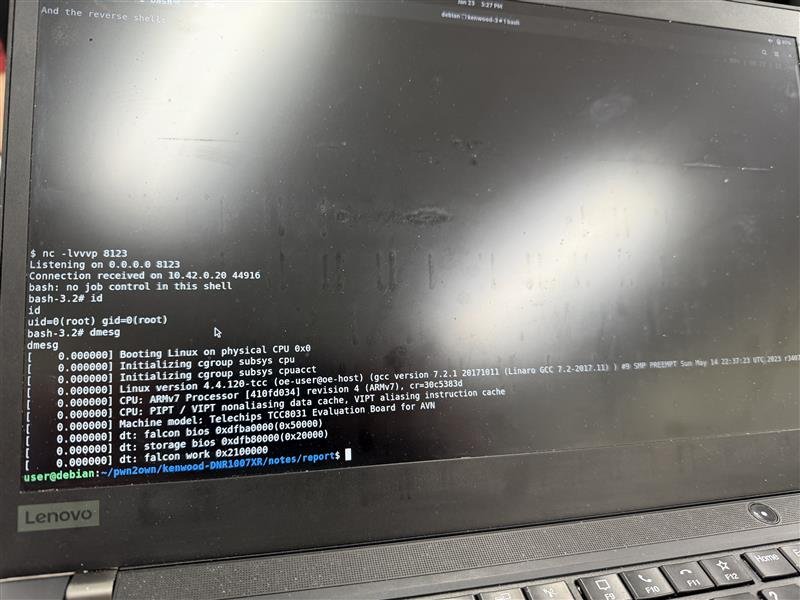
SUCCESS / COLLISON - Team MST targeted the Kenwood DNR1007XR, demonstrating one bug but running into a collision, earning $2,500 USD and 1 Master of Pwn point.
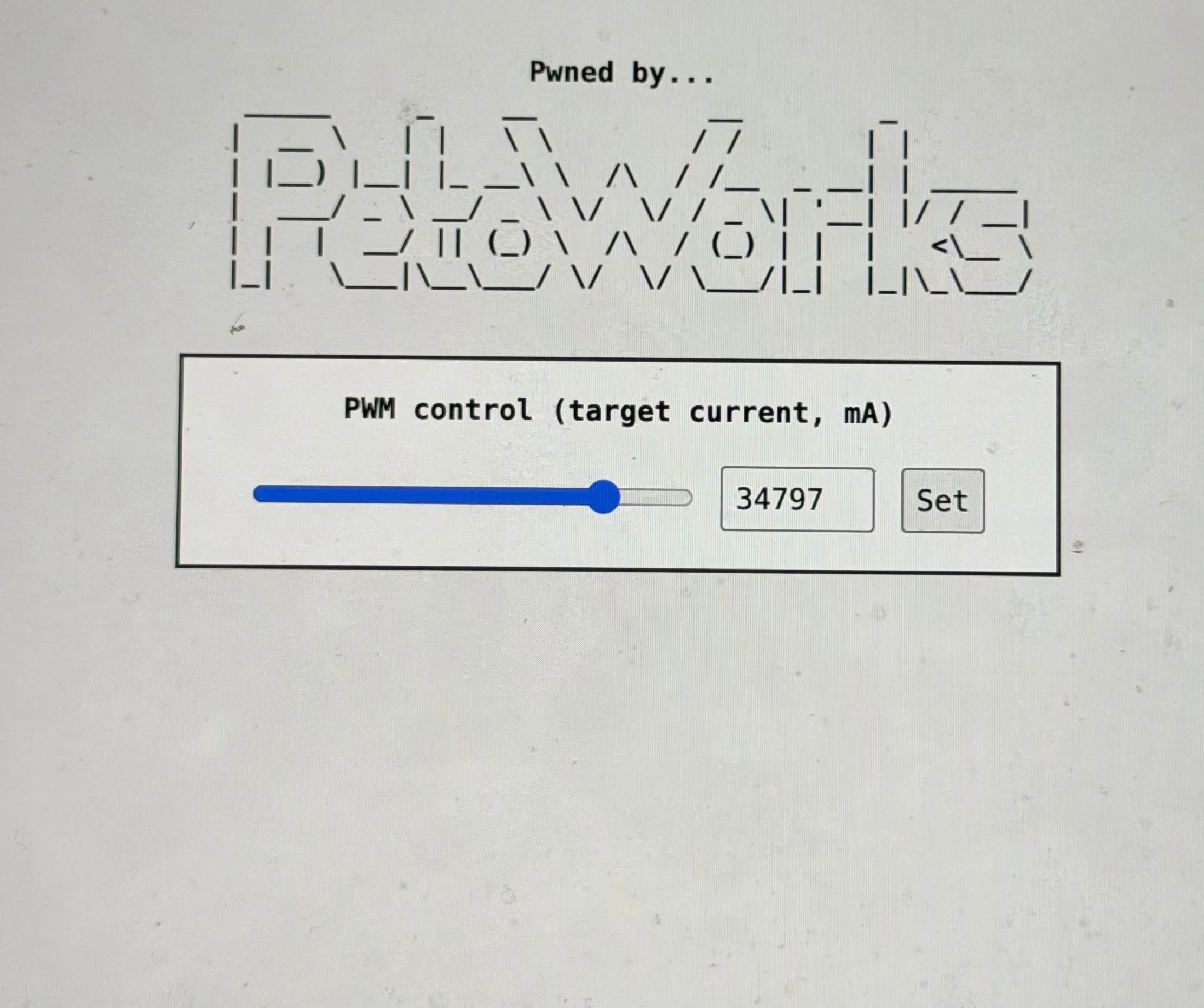
SUCCESS - PetoWorks (@petoworks) targeted the Grizzl-E Smart 40A, exploiting one buffer overflow bug, and earned $10,000 USD and 4 Master of Pwn points.
SUCCESS - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS targeted the Alpine iLX‑F511, exploiting a stack‑based buffer overflow to earn $5,000 USD and 2 Master of Pwn points.
SUCCESS - Viettel Cyber Security (@vcslab) targeted the Sony XAV‑9500ES, exploiting a heap‑based buffer overflow to achieve arbitrary code execution, earning $10,000 USD and 2 Master of Pwn points. #Pwn2Own #P2OAuto
SUCCESS / COLLISON - Qrious Secure (@qriousec) targeted the Kenwood system, demonstrating three bugs - one n-day and two unique vulnerabilities (incorrect permission assignment and a race condition), earning $4,000 USD and 1.75 Master of Pwn points.
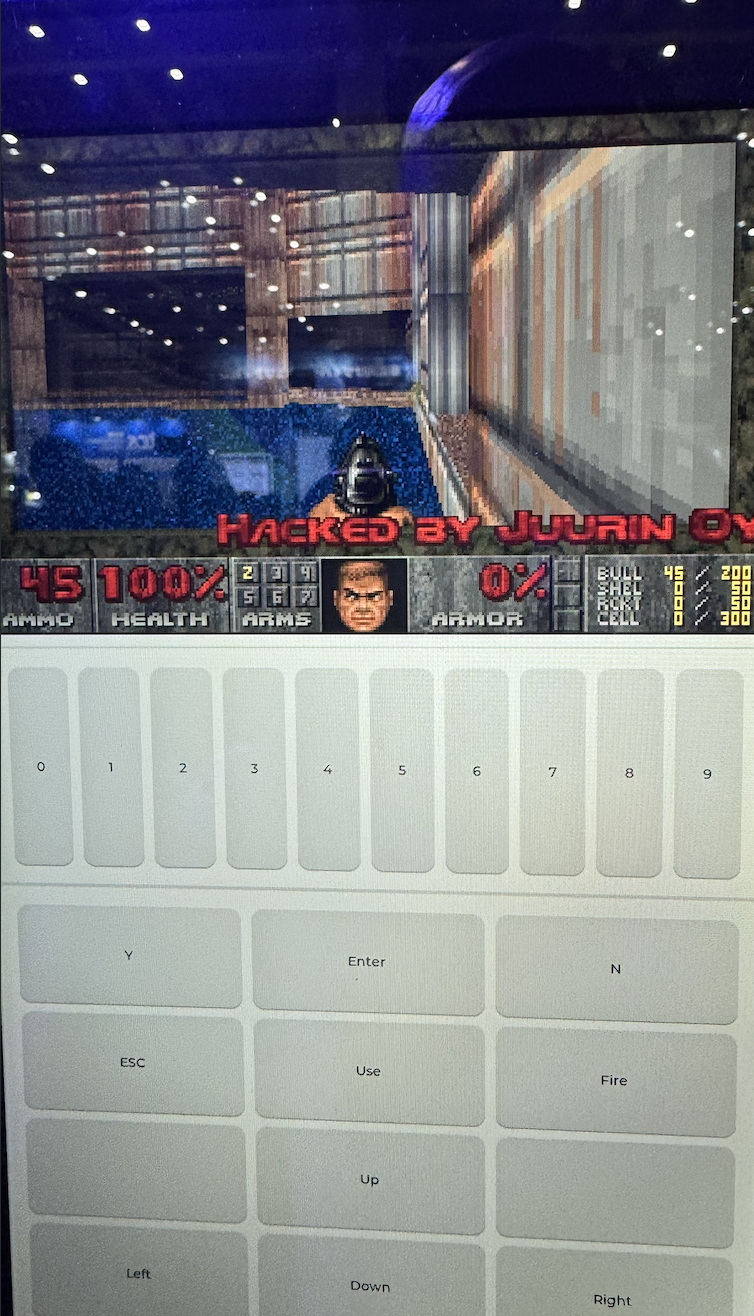
SUCCESS - Boom! or shall we say Doom? Game On! Aapo Oksman, Elias Ikkelä-Koski and Mikael Kantola of Juurin Oy exploit the Alpitronic HYC50 with a TOCTOU bug - and installed a playable version of Doom to boot. They earn $20,000 and 4 Master of Pwn points. #Pwn2Own #P2OAuto
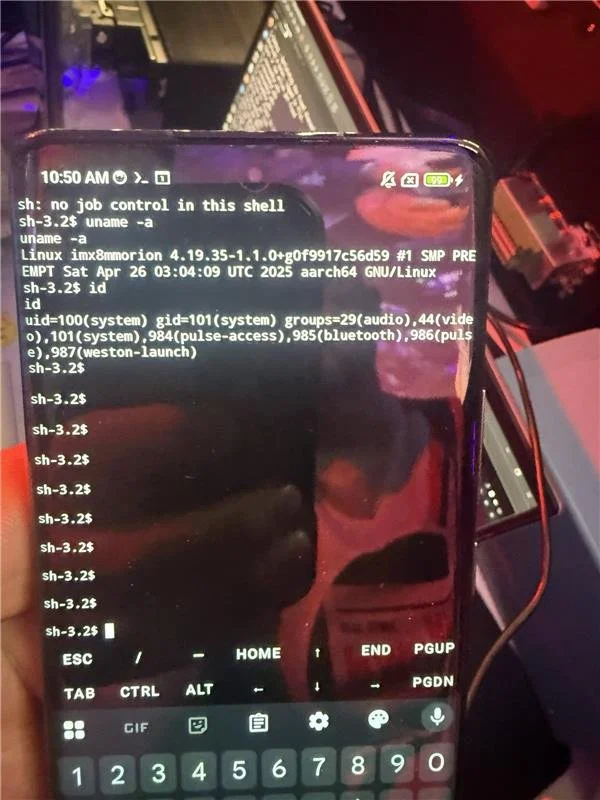
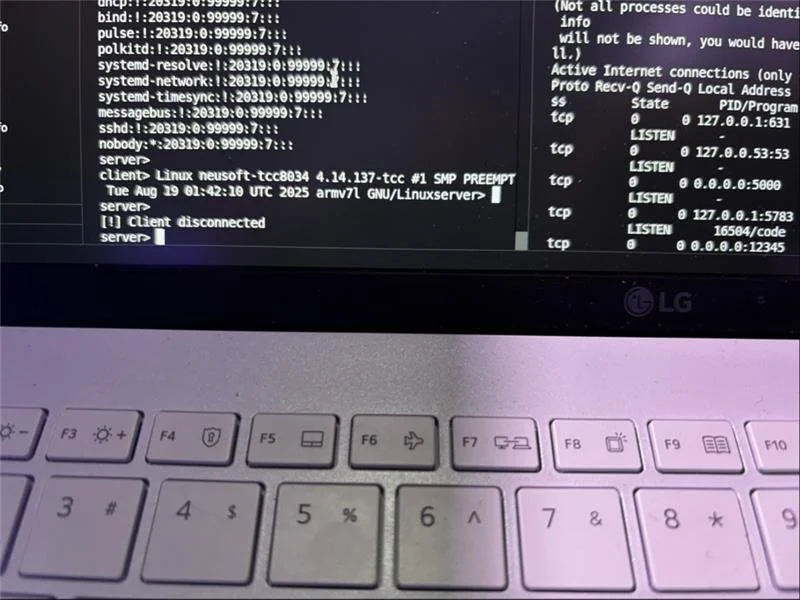
SUCCESS / COLLISON - Nguyen Thanh Dat (@rewhiles) of Viettel Cyber Security (@vcslab) targeted the Kenwood DNR1007XR, demonstrating one bug but encountering a collision, earning $2,500 USD and 1 Master of Pwn point.
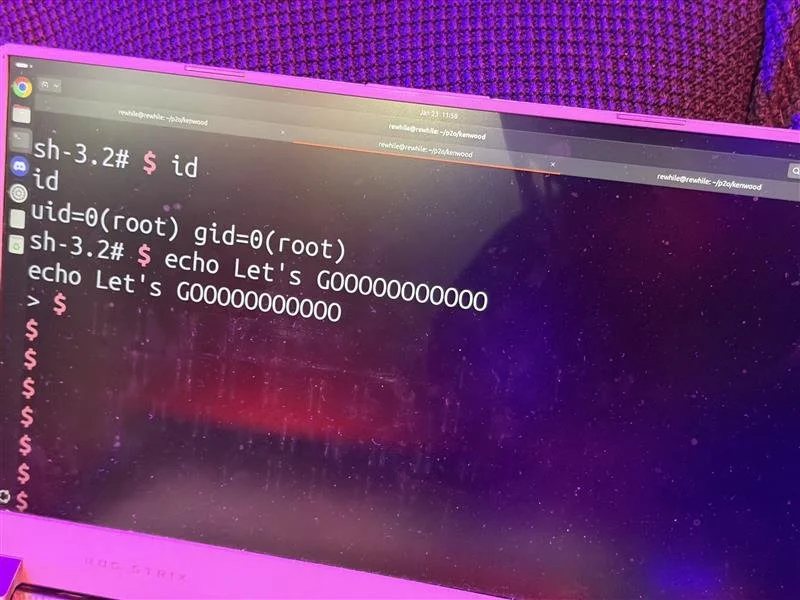
SUCCESS / COLLISON - Autocrypt (Hoyong Jin, Jaewoo Jeong, Chanhyeok Jung, Minsoo Son, and Kisang Choi) targeted the Alpine iLX-F511, demonstrating two vulnerabilities to gain root access. One collided with a previously known issue, earning $3,000 USD and 1.25 Master of Pwn points.
SUCCESS - Elias Ikkelä-Koski and Aapo Oksman of Juurin Oy targeted the Kenwood DNR1007XR, demonstrating a link-following vulnerability to earn $5,000 USD and 2 Master of Pwn points.
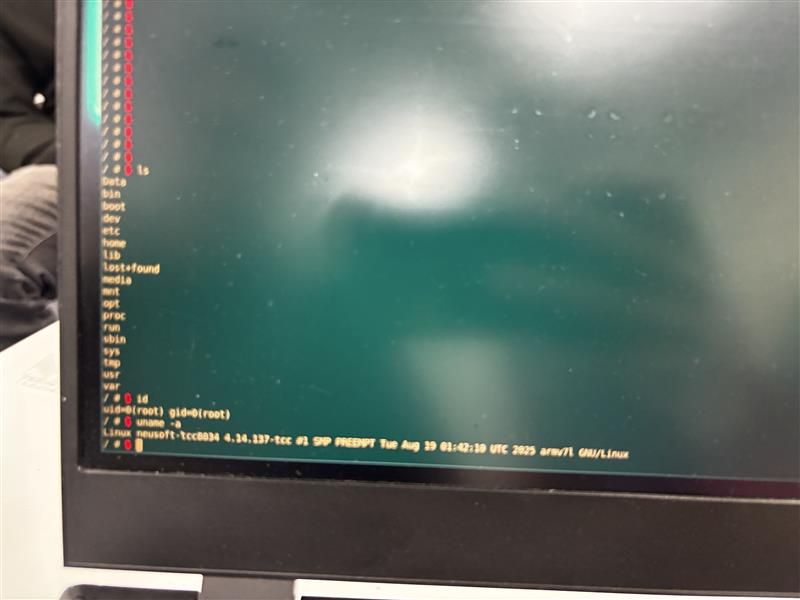
SUCCESS - Nam Ha Bach and Vu Tien Hoa of the FPT NightWolf Team targeted the Alpine iLX-F511, exploiting one unique vulnerability to gain root access and earning $5,000 USD and 2 Master of Pwn points.
SUCCESS / COLLISON - Ryo Kato (@Pwn4S0n1c) targeted the Autel MaxiCharger AC Elite Home 40A, demonstrating a three-bug chain but encountering one collision, still earning $16,750 USD and 3.5 Master of Pwn points.